Introdution
# 把封包上面的destionation ip轉成內部ip
DNAT: Destination Network Address Translation.
Translates the destination IP address of incoming traffic to an internal server’s address.
Configuration
[1]
Login FortiGate WebUI > Policy & Objects > Virtual IPs > Create New
[2]
# 選any會有hairpin NAT的問題
Interface: "any" or "wan1(specific)"
# 選擇要哪一種形式的VIP
Type: Static NAT / FQDN
# 不一定要是介面上的IP
External IP address/range: "Your VIP"
# 內部映射到的IP
Map to IPv4 address/range: "Your internal IP"
# 是否要Port Forwarding > 外部轉到裡面是不同Port
Protocol: TCP / UDP / SCTP / ICMP
External service port: 4433
Map to IPv4 port: 1433
[3]
Policy & Objects > New Policy > Destination:(VIP)
TroubleShooting
1.
# 確認FortiGate是否有正常接收到去程流量
diagnose sniffer packet wan1 'host 20.20.20.20 and port 23' 4 0 a
2.
# 確認FortiGate是否有正常接收到流量並且做出正確的DNAT轉發
diagnose debug flow filter saddr 20.20.20.20
diagnose debug flow filter dport 23
diagnose debug flow show function-name enable
diagnose debug flow trace start 100
diagnose debug enable
> msg="check failed on policy": 表示VIP失敗
> msg="DNAT 20.20.20.20 0:23->192.168.1.1:23": 表示DNAT成功
3.
# 確認DNAT回程的流量是否有正常進入FortiGate
diagnose sniffer packet internal 'host 192.168.1.1 and port 23' 4 0 a
Further Reading
# Session套用到DNAT時,會一起建立回程的SNAT
diagnose sys session list
>
Src: 192.168.1.1
VIP: 192.168.1.100 > 10.10.10.1
Dst: 10.10.10.1
>
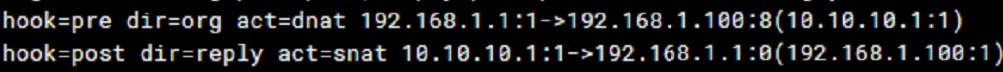
# hook=pre: pre-routing 階段,也就是封包剛進 FortiGate 時,還沒經過 policy / NAT 決策前。
# hook=post: post-routing 階段,也就是封包已經經過 policy 檢查、NAT 決策後,準備要送出介面的時候。
# dir=org: 去程方向,來源>目的
# dir=reply: 回程方向,目的>來源
